sigrok + UNIX = Awesome!
I've decided it's time to start blogging about the power of sigrok when used together with all the other tools on a typical UNIX machine. This sort of thing usually wouldn't be documented, because it's not really sigrok functionality, but for me these are the most powerful tricks of all.
Here's an example...
Example I - LogicPort BitBanging
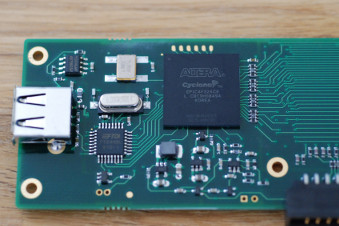
Lee Jones has recently started working on a driver for the Intronix LogicPort. The original manufacturer has declined to provide any documentation about the protocol, so Lee has been working hard on reverse engineering it.
The LogicPort internally consists of a Altera EP1C4F324C6 FPGA, with a FTDI FT245BL USB interface.
For USB devices, our typical workflow is to run the vendor software inside a Windows VM and setup a USB passthrough. Then, in the Linux host machine we use usbmon (sometimes via Wireshark) to inspect the packets sent and received. To implement a driver, the developer must then try to replicate this protocol in the driver.
Lee discovered that early in the process of initialising the device, a large block of binary data is sent by the PC to the device. This is a hexadecimal dump of just the beginning part of the packet:
05070507 05070507 05070507 05070507 05070507 05070507 05070507 05070507
04060507 04060507 05070507 04060406 05070507 04060406 04060507 04060507
04060406 05070507 05070406 04060406 04060406 05070507 05070406 04060406
....
We suspected that this data is actually being used to cause the FTDI chip to bit-bang an SPI waveform to configure the FPGA. But how can we get more clarity? Answer: with sigrok.
-
First we need to convert this hexadecimal data to binary. xxd has a handy reverse mode that can input hex, and output binary:
-
xxd -r -p dump.txt > dump.bin
-
-
PulseView has basic support for importing binary data; currently it will assume any file ending in .bin is 8-probe logic data. Opening the file in PulseView, we can see the waveform clearly:

PulseView now also has very basic support for protocol decoding, which allows us to see the bytes of SPI data.
-
Pretty though PulseView decoding is, sigrok-cli is actually more powerful in the end, because with sigrok-cli we can extract the actual bytes from the SPI data stream. Currently sigrok-cli has some problems with its binary input module (these are being addressed in bug #166), so this has to be done in two steps:
-
First, convert the binary data to a sigrok session file:
-
sigrok-cli -I binary:numprobes=2 -i dump.bin -o dump.sr
-
-
Second, do the decode from the session file:
-
sigrok-cli -i dump.sr -P spi:mosi=0:sck=1
-
Data is decoded:
-
spi: "FF/1FFE" spi: "FF/1FFE" spi: "5C/1FFE" .....
-
-
-
Finally we can use some UNIX magic to extract the firmware binary:
-
sigrok-cli -i dump.sr -P spi:mosi=0:sck=1 | cut -c7-8 | xxd -r -p > firmware.bin
- (One day sigrok-cli will acquire a feature to decode directly into binary, but for now this pipeline works fine)
-
-
First, convert the binary data to a sigrok session file:
I think this stuff is really cool. I'm out of time for now, but I'll try and write up some more examples in following posts.
- Joel Holdsworth's blog
- 10334 reads